NDR
Network Detection and Response
CYBER COMMAND
Network Detection and Response platform to detect and respond to cyber threats
Network Detection and Response improves the ability to detect and respond to cyber threats that could affect the company. This, by monitoring internal network traffic and correlating security events thanks to Artificial Intelligence.
- Network detection and response capabilities towards threats thanks to internal network traffic monitoring.
- Cyber Command correlates security events by applying AI, behavior analysis and global threat intelligence.
- Cyber Command finds out not only already existing security violations, but also hidden threats in the company’s network
- Cyber Command integrates network security and endpoint solutions to respond to threats automatically.

Increase IT security in your company with Network Detection and Response
Poor cyber threat prevention allows attacks to bypass security controls.
Regardless of the security technology adopted, misconfiguration or lax controls are often the weakest points of corporate cybersecurity management.
Companies’ cyber security management requires time and skills
If many alerts are generated, security management becomes time-consuming and difficult for administrators to master.
Cyber Command, an NDR platform, discovers security control violations and integrates both network and endpoint cybersecurity solutions, dramatically improving the ability of enterprise IT leaders to analyze and understand the global threat landscape.
The lack of visibility into the company’s security posture makes it difficult to evaluate effective countermeasures
Despite firewalls or EDR clients, attacks can still succeed as cyber attackers find new attack vectors every day. This is because devices of which the IT department has no visibility could be connected in the local networks. These can be used to attack the company. In fact, through AI, a malicious actor manages to evade control with increasingly targeted attacks.
To increase the security level of the corporate infrastructure, it is essential to adopt a Network Detection and Response solution.
As a result of cyberattacks, data thefts, and the resulting service interruptions, these incidents can result in significant damages to the privacy of customers of the victims, as well as to the image and reputation of the organization as a whole, which may lead to loss of both customer and investor confidence.
What is Cyber Command for?
This NDR (powered by Sangfor Technologies) platform offers a number of cybersecurity and threat detection benefits.
Cyber Command is connected with Threat Intelligence and with attacks at all levels of the chain. This means early warnings as a result of:
- Exploitation attempts
- Slow brute force attacks
- C&C activity
- Horizontal movements
- P2P traffic
- Data theft
Golden eye: cyber threats detection
Cyber Command, thanks to its “golden eye” function, studies the behavior of compromised corporate resources and uses this information to strengthen the system’s external and internal defenses.
Integrations
Changing your company’s cybersecurity infrastructure can be challenging, which is why Cyber Command is compatible with most devices and platforms. You will be able to maintain your systems and integrate them easily with Cyber Command.
Elimination of blind spots
A common problem many organizations face is the inability to see threats spreading horizontally across their network. Cyber Command boasts 100% visibility of East-West and North-South traffic: the platform monitors, analyzes, detects threats and decrypts data, also using AI to discover suspicious behavior.
STA (Stealth Threat Analysis)
Existing security solutions can block 99% of malware, but thousands of new variants bypass security devices every day. Cyber Command can detect that 1% using a sensor that collects raw network traffic from switches, extracts security events, and detects anomalous behavior.
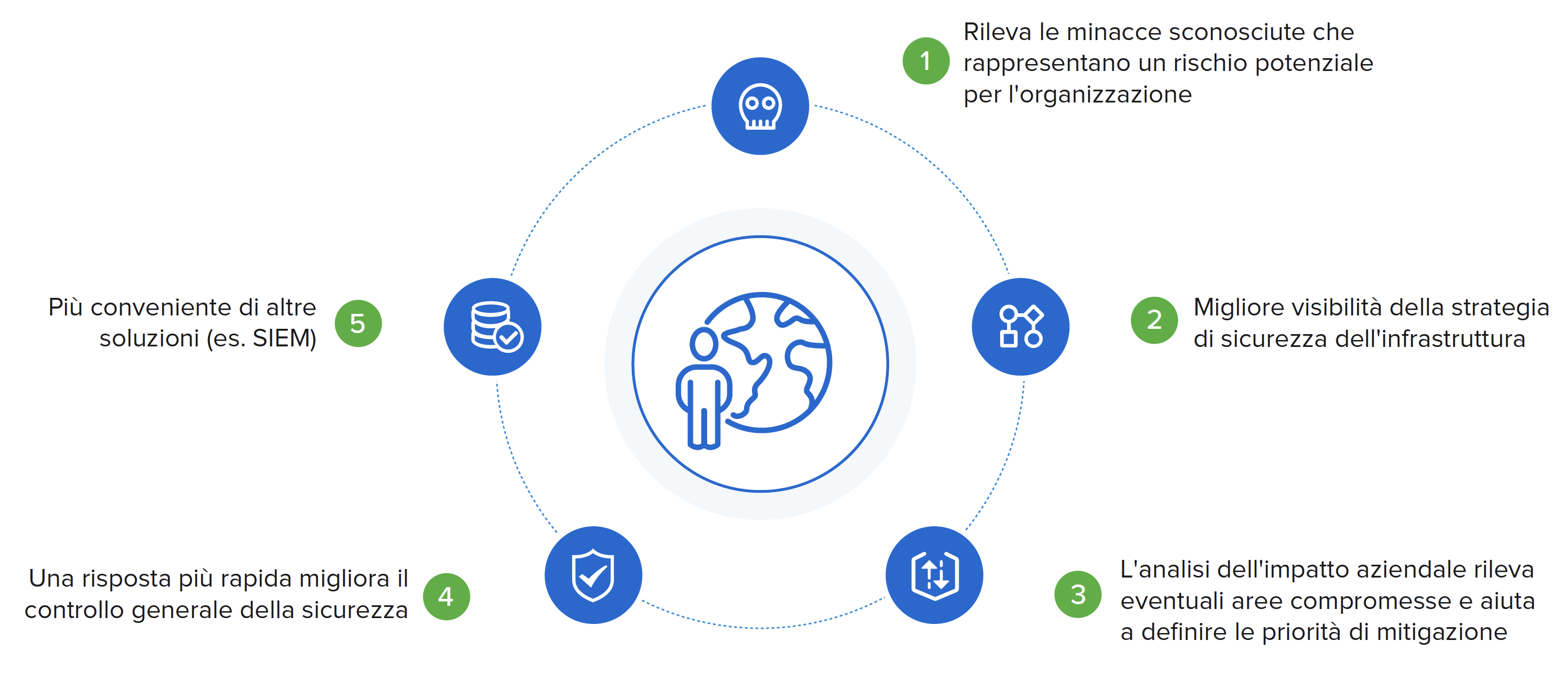
SOLUTION’S BENEFITS
PLATFORM USE CASES
Cyber Command improves overall IT security by implementing advanced network detection and response (NDR) protocols
Ransomware/ Bitcoin Mining – security incident
- Cyber Command uses a timeline to trace the attack from the point of entry and provides the root cause
- AI and Machine Learning algorithms help Cyber Command detect hidden threats and C&C communications, automatically stopping ransomware propagation
- The platform ensures that the company sees all the risks that could arise due to compromised business assets
Detection and ongoing response to cyber threats
- Integration with network and endpoint security technologies to provide detailed threat analysis and response.
- The latest algorithms automatically combine network logs, reduce alerts and increase productivity.
- AI-powered policy analysis and real-time monitoring ensure corporate assets are protected from new threats.
Insider Threats and Privileged Account Breaches
- Effective detection and response to external and internal threats. Network traffic analysis (NTA) and user and entity behavior analysis (UEBA) can identify and alert on suspicious activity like malicious external DDoS attacks, botnet domain generation algorithms, and abnormal user behaviors. These technologies are essential for effective detection and response to threats both external and internal.









